Wireshark Cheatsheet
Filtering Captures
Here is a link to detailed Wireshark Documentation regarding specific filtering operands/uses.
Common Operators:
| Operator | Command | Alt. Command |
|---|---|---|
| AND | and |
&& |
| OR | or |
|| |
| GREATER THAN | gt |
> |
| LESS THAN | lt |
< |
| GREATER THAN OR EQUAL TO |
ge |
>= |
| LESS THAN OR EQUAL TO |
le |
<= |
| EQUALS | eq |
== |
| NOT EQUALS | ne |
!= |
| CONTAINS | contains "xxxx" |
|
| MATCHES | matches |
~ |
| BITWISE_AND | bitwise_and |
& |
Here is an example of specific usage for the last three:
| Expression | Description | Usage |
|---|---|---|
| contains | Protocol, field or slice contains a value | sip.To contains "a1762" |
| matches | Protocol or text field matches a Perl-compatible regular expression | http.host matches "acme\\.(org|com|net)" |
| bitwise_and | Bitwise AND is non-zero | tcp.flags & 0x02 |
Basic Filtering by Protocol/Service:
# Filter by IP Address
ip.addr == xxx.xxx.xxx.xxx
# Filter by IP Source & Destination
ip.src == xxx.xxx.xxx.xxx && ip.dst == xxx.xxx.xxx.xxx
# Filter by Port # or Service Name
tcp.port == 80 or http #Note: giving only a service name here throws an *invalid number* error
udp.port == 3389 or rdp
Use Case:
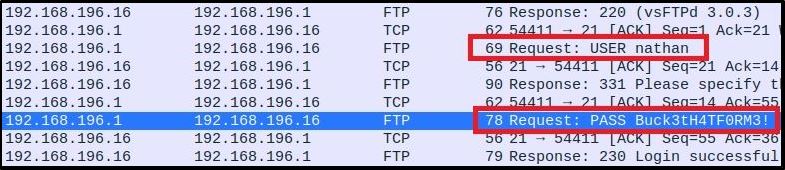
I recently completed a virtual machine from HackTheBox (Write-Up Here) where I was able to exploit an indirect object reference to obtain an old PCAP (Packet Capture) file from the hosts webserver.
After doing my port scan, I knew that Port 21 (FTP) and Port 22 (SSH) were both open on the machine. This would be a great opportunity to load the PCAP into Wireshark and then filter-by-port for known service traffic like so:
tcp.port == 21 or ftp
tcp.port == 22 or ssh
You can see in this screenshot that plaintext credentials were found in FTP traffic: